Stop doing bad audits
Heyo,
Jules here, from the Cyfrin team.
The difference in assets stolen between audited and unaudited contracts is astounding.
Good news is: anyone with some technical background can perform security reviews.
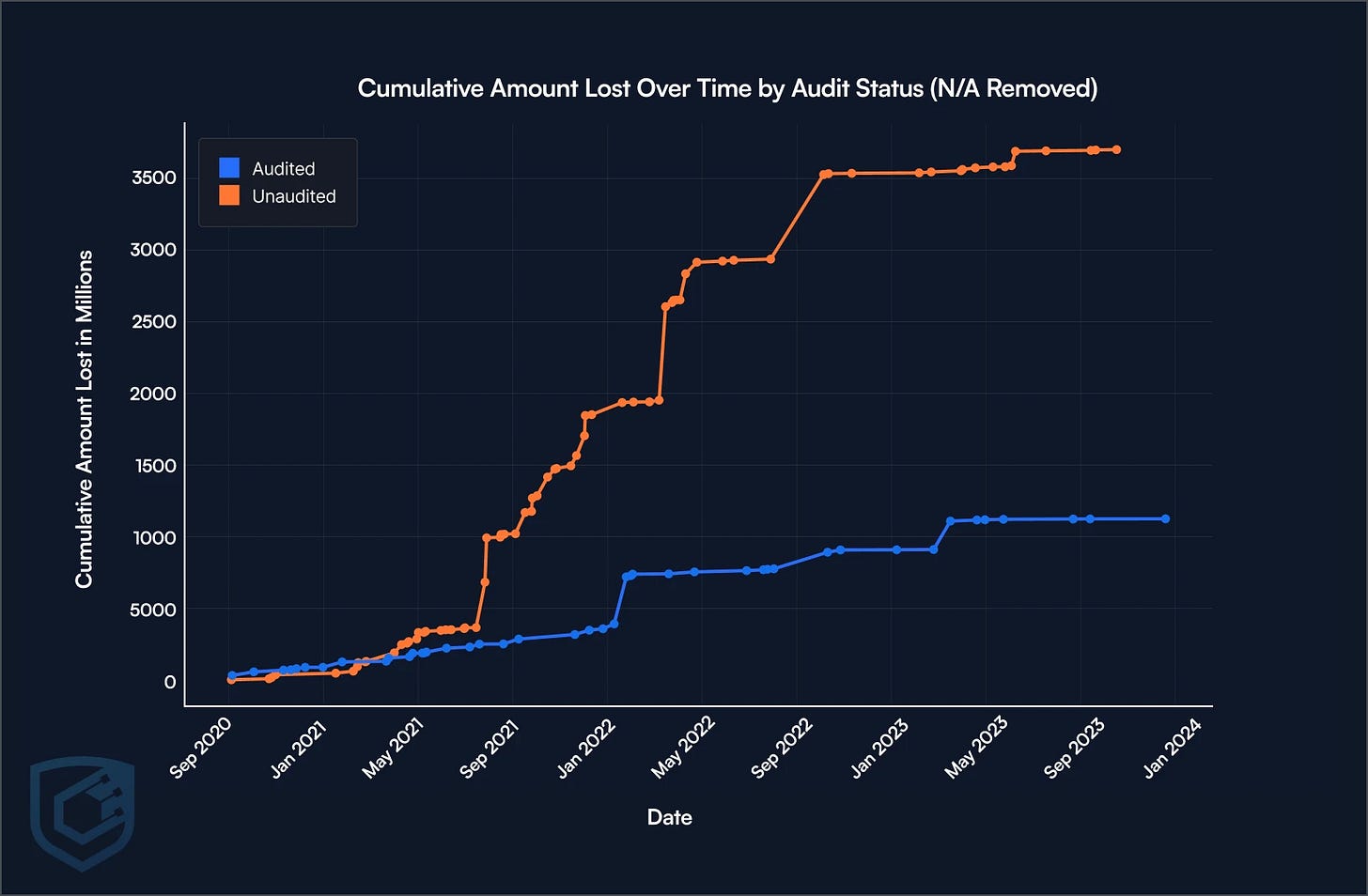
Source: Rekt Leaderboard
Here are 10 tips to audit smart contracts
1 🗺️ Gain codebase context, aka read the docs
Read docs, digest audit scope, and spend time understanding the business logic behind what the protocol is intended to do. Don’t skip this.
2 📖 Run all README methods
Run the project locally and look out for any warnings, packages, or interesting messages the terminal may throw.
3 🕵🏻♀️ Run tests
Tests are a window into what the protocol considers important. Checking code coverage also helps to spot where the weaker areas may be.
4 🔌 Digest the codebase in chunks, start a protocol mental model
Sometimes this means a high-level diagram of the architecture and entry points. Other times it means the nitty gritty of what a function is meant to do. Both are important.
5 👵🏻 Check the versions of each contract
Is the protocol using the latest Solidity version or an older one? What common bugs are known for that specific version? Does this code utilize any similar patterns?
6 📚 Leverage Solodit for previous findings
Solodit is a vulnerabilities aggregator indexing bugs found in previous audits. It’s helpful to look for bugs found in other contracts doing something similar things or having similar dependencies.
7 👩🏻🎤 Get familiar with roles, access controls, function parameters, and entry points
Anything that has a public or external attribute, dependencies on other contracts, or state changes — anything that triggers behavior changes based on inputs are prompt to malicious entry points.
8 ⚡️ Function nitty gritty
What is the function expected to do vs what it actually does? Often bugs are not in the lower-level complexities, but in how the business logic expects the code to work.
9 ⚒️ Leverage tools like Aderyn or Slither
Most auditors today are using these, so findings won’t be unique or critical. However, they help in providing an idea of where some of the codebase weaker points may be.
10 👩🏻🏫 Make your report pop
It’s your job as an auditor to prove to the judge that your bug exists. Writing proofs of code (PoC), solid titles (<ROOT CAUSE>-<IMPACT> is a good formula), and good documentation all help!
If white hacking peaks your interest, learn how to audit smart contracts with Updraft - web3 developer education platform.
Join for early access today: https://x.com/CyfrinUpdraft/status/1722253512741101648?s=20
Keeping up with Web3 security
Web3 Salaries: how much do auditors really make?
Slowmist released a learning roadmap for becoming a smart contract auditor
What is formal verification testing (FV) and how does it compare to fuzzing?
Q3 2023 crowned most ‘damaging’ quarter for crypto amid $700M losses
Let me know if you have any questions, happy to help!
Sending cyber love,
Jules 🤸🏻



